[ad_1]
Getty Pictures
From the what-could-possibly-go-wrong recordsdata comes this: An industrial management engineer just lately made a workstation a part of a botnet after inadvertently putting in malware promoting itself as a way for recovering misplaced passwords.
Misplaced passwords occur in lots of organizations. A programmable logic controller—used to automate processes inside factories, electrical vegetation, and different industrial settings—could also be arrange and largely forgotten over the next years. When a alternative engineer later identifies an issue affecting the PLC, they will uncover the now long-gone authentic engineer by no means left the passcode behind earlier than departing the corporate.
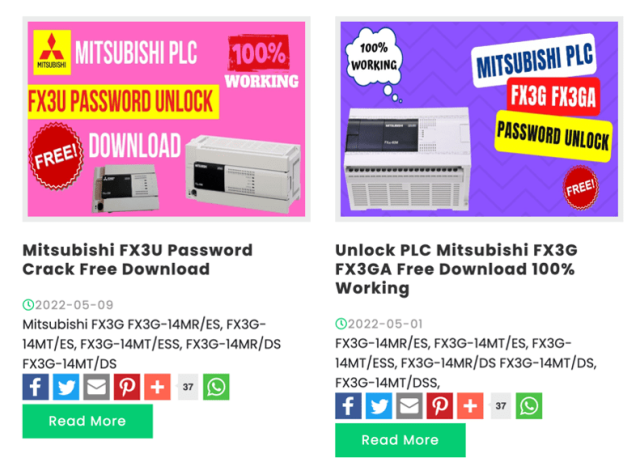
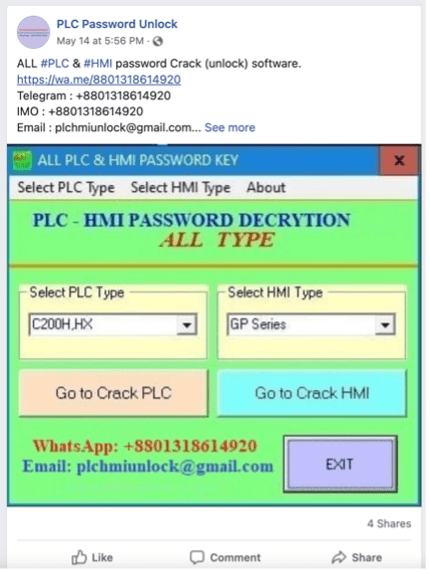
In line with a blog post from safety agency Dragos, a whole ecosystem of malware makes an attempt to capitalize on situations like this one inside industrial services. On-line commercials like these under promote password crackers for PLCs and human-machine interfaces, that are the workhorses inside these environments.
Dragos
Dragos
When your industrial system is a part of a botnet
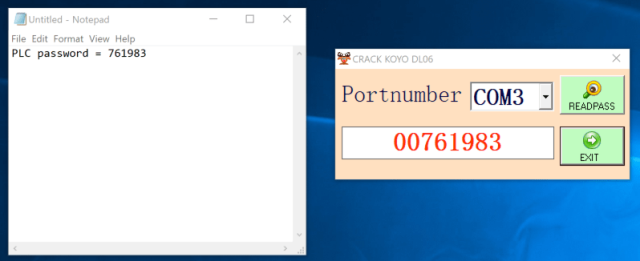
Dragos—which helps companies safe industrial management techniques in opposition to ransomware, state-sponsored hackers, and potential saboteurs—just lately carried out a routine vulnerability evaluation and found a buyer’s system had run software program that was capable of efficiently recuperate the plaintext password for the DirectLogic 06, a PLC bought by Automation Direct. The software program recovered the password, however not by the traditional technique of cracking the cryptographic hash. As a substitute, the software program exploited a zero-day vulnerability in Automated Direct PLCs that uncovered the passcode.
Dragos
“Previous research targeting DirectLogic PLCs has resulted in profitable cracking methods,” Dragos researcher Sam Hanson wrote. “Nevertheless, Dragos discovered that this exploit doesn’t crack a scrambled model of the password as traditionally seen in common exploitation frameworks. As a substitute, a selected byte sequence is distributed by the malware dropper to a COM port.”

Dragos
The vulnerability, and a associated one additionally discovered by Hanson, have now been patched and are tracked as CVE-2022-2033 and CVE-2022-2004. The latter vulnerability can recuperate passwords and ship them to a distant hacker, bringing the severity ranking to 7.5 out of a potential 10.
Apart from recovering the password, the software program put in on the Dragos buyer’s community additionally put in malware often known as Sality. It made the contaminated system a part of a botnet and monitored the clipboard of the contaminated workstation each half second for any knowledge associated to cryptocurrency pockets addresses.
“If seen, the hijacker replaces the handle with one owned by the menace actor,” Hanson mentioned. “This in-real-time hijacking is an efficient technique to steal cryptocurrency from customers eager to switch funds and will increase our confidence that the adversary is financially motivated.”
Hanson went on to say that he has discovered password crackers marketed on-line for a variety of commercial software program bought by different firms. They embrace:
| Vendor and Asset | System Kind |
| Automation Direct DirectLogic 06 | PLC |
| Omron CP1H | PLC |
| Omron C200HX | PLC |
| Omron C200H | PLC |
| Omron CPM2* | PLC |
| Omron CPM1A | PLC |
| Omron CQM1H | PLC |
| Siemens S7-200 | PLC |
| Siemens S7-200 | Mission File (*.mwp) |
| Siemens LOGO! 0AB6 | PLC |
| ABB Codesys | Mission File (*.professional) |
| Delta Automation DVP, ES, EX, SS2, EC Collection | PLC |
| Fuji Electrical POD UG | HMI |
| Fuji Electrical Hakko | HMI |
| Mitsubishi Electrical FX Collection (3U and 3G) | PLC |
| Mitsubishi Electrical Q02 Collection | PLC |
| Mitsubishi Electrical GT 1020 Collection | HMI |
| Mitsubishi Electrical GOT F930 | HMI |
| Mitsubishi Electrical GOT F940 | HMI |
| Mitsubishi Electrical GOT 1055 | HMI |
| Professional-Face GP Professional-Face | HMI |
| Professional-Face GP | Mission File (*.prw) |
| Vigor VB | PLC |
| Vigor VH | PLC |
| Weintek | HMI |
| Allen Bradley MicroLogix 1000 | PLC |
| Panasonic NAIS F P0 | PLC |
| Fatek FBe and FBs Collection | PLC |
| IDEC Company HG2S-FF | HMI |
| LG Okay80S | PLC |
| LG Okay120S | PLC |
Dragos examined solely the malware focusing on the DirectLogic gadgets, however a rudimentary evaluation of some samples indicated in addition they contained malware.
“Usually, it seems there’s an ecosystem for such a software program,” Hanson mentioned. “A number of web sites and a number of social media accounts exist all touting their password ‘crackers.’”
The account is regarding as a result of it illustrates the laxness that continues to function in lots of industrial management settings. The criminals behind the malware infecting the Dragos buyer had been after cash, however there’s no cause extra malicious hackers out to sabotage a dam, energy plant, or related facility couldn’t carry out an identical intrusion with rather more extreme penalties.
Source link


